The Internet – that technological wonder of World Wide communication has spun a whole new “WEB” of liability exposures for individuals and businesses. It’s a fact that many retail furniture operations haven’t thought about, but should.
Prior to 1984, computers were BIG, costly central systems owned by large companies. Remember COBOL or Fortran?
Personal Computers (PCs) did not exist except as games. Remember playing Pong?
In 1982 the first PC was introduced by IBM. Macintosh Apple followed in 1984. Today 75.6% of US households own a PC. 30,000,000 pay their bills via the Internet and 50,000,000 bank online. Over 50 percent of the US population shops and buys online generating about $1 trillion in sales yearly. Internet traffic in the US has, ,increased 15 percent every year for in the past 10 years, generated 12 trillion emails. There are more than 150,000,000 websites internationally that sell a product, distribute information or provide a service to 1.6 billion people.

Today the news is full of stories about threats directed against countries and large businesses including media giants, financial institutions and technology companies. And although high level hackers may not be targeting your store specifically, you are still at risk of loss from a number of internal and external exposures including:
Direct Damage or Destruction of your systems software and electronic data by outside sources.
These include fire, wind, vandalism, flood, system malfunction, program errors, employee error, or intentional acts of others such as a Virus, Worm, or Trojan Horse.
- Virus – A small piece of software that piggybacks on real programs. Once it is running, it can spread to other programs and documents.
- Worm – A small piece of software that uses computer networks and security holes to replicate itself.
- Trojan Horse – a computer program that claims to do one thing, but actually does damage when it is run.
In 2000, the ILOVEYOU virus attacked hundreds of corporate computers at a cost of billions of dollars in lost income and additional programming needs.
Loss of Income due to the suspension of your business.
Your liability subsequent to damage from outside sources is the cost to reprogram and restore data. Also, your system may be shut down due to a Virus threat, Denial of Service Attacks (system saturated with outside requests causing it to be unresponsive), Mail Bombs (website receives emails from a bogus source which explode upon opening).
Recently a dealer’s website was vandalized by hackers who installed profane language. The site was shut down for many days. $1,800,000 was the cost to restore the site including loss of income.
Loss of Market Share.
This could certainly result from the suspension of your operations or bad publicity following a loss.
Remember Circuit City? In September 2008, 6,000,000 Circuit City credit card holders were notified that computer files containing personal information was mistakenly thrown out. Just recently Target lost credit and debit card information for 40 million customers, as well as the names, addresses, and phone numbers of many more. The result was huge negative publicity for the retailer.
Theft of a Customer's Personal Data.
In 2006 laptops were stolen from three Sovereign Bank employees’ vehicles that contained customers’ personal data. The bank was forced to advise thousands of customers that their personal data was at risk.
Damage to Someone Else’s Data or Software and Subsequent Loss of Income.
What if your company accidentally transmits a virus or faulty data to a customer or supplier?
- Perhaps a disgruntled employee intentionally acts maliciously by transmitting a virus to a customer via your email system.
- Or, your company's website that is considered secure has its email system infected by a virus. An employee transmits this via email to several customers. Those customers then file claims against you for the cost of cleansing their systems.
- Theft of Money or Intellectual Property.
- One of your employees uses their personal computer to access the company's customer database.
- The information is then sold to a competitor or a computer hacker who gains access to company files and steals your software development programs.
- Extortion.
- A hacker might scramble codes, encrypt programs then hold your data for ransom.
- One of your employees or someone else could demand money under the threat of unleashing a virus that would delete information or release confidential information over the Internet.
- Or, you might receive an email claiming that the sender has penetrated your firewall and copied customer’s credit card information. The sender threatens to post the information on the Internet unless $1,000,000 is received within hours.
- Defamation.
- Employee sends an email to company officers questioning a vendor’s professionalism. The officers distribute the email throughout the company. After learning of this email the vendor sues you alleging defamation.
- You launch a new website that includes unfavorable remarks about one of your competitors. The competitor then sues alleging defamation.
- Infringement.
- Your company posts files that contain copyrighted clip art on its web page. The owner of the clip art sues for infringement.
- You attempt to increase the hit ratio on your website by listing several famous lines on the Meta tag even though you do not represent them. One of the lines sues for trademark infringement.
Invasion of Privacy.
One of the nation's largest health insurers inadvertently sent emails to members containing confidential medical and personal information of other members. Lawsuit filed for millions of dollars alleging invasion of privacy.
Harassment.
- An employee posts a joke on your company's email that contains language that is offensive to female employees. One of these employees then sues alleging workplace harassment.
- Employee sends an email describing a certain customer as a hot babe. In addition he expresses a desire for a sexual relationship. However, the fellow employee who receives the email is not his friend and he forwards the email to the customer who then sues the company and employee for sexual harassment.

Identity Theft.
Certainly last but not least, identity theft is the most common exposure we see. Criminals steal information about a person to impersonate them and acquire credit under their names. The victims are then left with bad credit ratings and the cost to repair the damage may be considerable.
According to 2008 estimates there were 8.1 million victims of Identity Theft in the United States which had a $48 billion price tag. The average number of hours spent to recover from Identity Theft is 600.
How To Protect Your Business
Although the eRisk is still new to all of us including the insurance industry where coverage premiums currently trend high due to the “UNKNOWN” and lack of rate setting experience, the standard of the industry is being addressed by a few available endorsements:
- Identity Fraud Expense coverage for homeowners policies.
- Electronic Commerce for business policies.
- Electronic Data Liability for business policies.
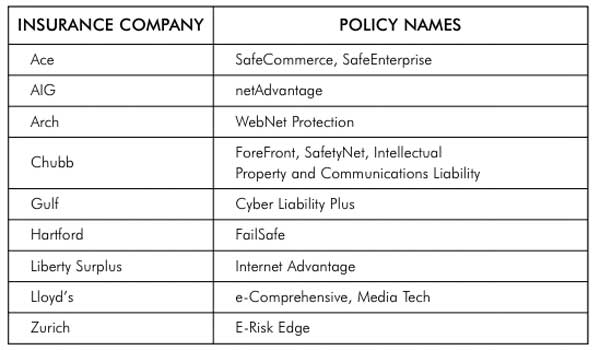
See the table above for a list of specialty carriers providing E-Commerce policies.
Building a website can be simple but the onslaught of exposures is not. Be prepared, as you venture on to the World Wide Web, realizing that the liability exposures you face are still emerging, evolving and complex.
I strongly suggest that you identify your particular exposures and to get a quote to determine the costs on this type of insurance to cover those exposures and your ASSets!